This is an old revision of the document!
Gateway and Firewall
Most people's home network is configured fairly simply, like this:
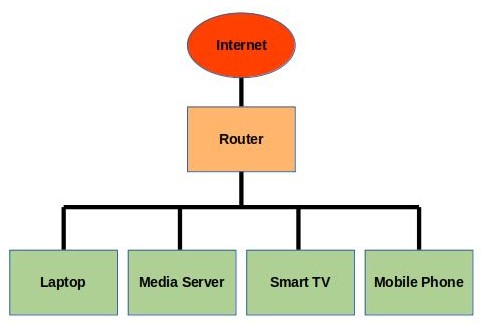
There's only one set of devices connected to the network, and they are all present in the same building.
What am I doing?
My domestic ADSL broadband router already provides the basic & essential functionality of a Gateway (with NAT) and a Firewall. So why do I want to make up my own way of doing things? The quick answer is I want to set up something far more interesting! I will still be using the functionality of the router, as that provides a good secure starting point.
The router also provides a forwarding DNS server and a DHCP server. I have already turned this functionality off and replaced it with my own configuration in a TrueNAS Jail.
The router also provides WiFi with WPA2 and PSK. I will be using this functionality without any change from me.
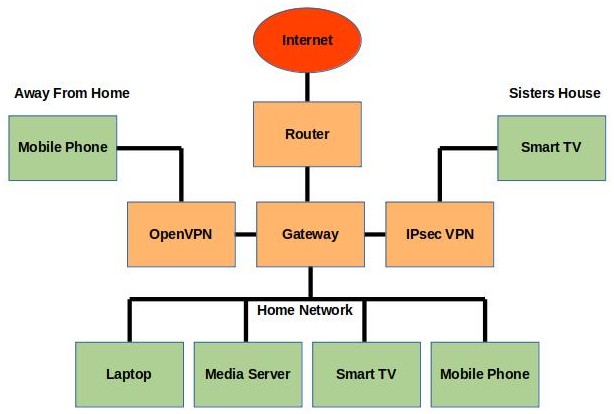
I plan to set up two different VPN servers on my TrueNAS box to enable me to seamlessly pass information between each of the devices I own, and also allow other members of my family to have restricted access some of the information stored on my home network.
The reason for the two different VPNs is that it is easier to set up one or the other depending on the devices that are being used. Microsoft platforms seem to favour IPsec, I've had a more reliable connection using OpenVPN on Android platforms. Some broadband routers have built-in support for one or the other, which means the router can handle a VPN connection directly, rather than having to set up extra hardware at my sister's place.
The DHCP and VPN servers will allocate specific IP addresses to individual devices. Each of the TrueNAS Jails (which provide different services) will be configured to use known static IPs. The firewall rules on the gateway will decide which devices on different networks are allowed to communicate with each other, and maybe allow access to the Internet via my home router.
The goal looks something like this:
Two Network Interfaces
You will need to set up a Jail that has two VLAN interfaces. One will be used for your LAN and the other will just be used to connect to your Internet router. In order to do this, you'll need to configure the interfaces in “Network Properties” of the Jail to say something like:
vnet0:bridge0,vnet1:bridge0
That will define two virtual network interfaces within the Jail, both bound to the first (probably only) physical network adapter on the TrueNAS box. You can then define two separate interfaces in the “Basic Settings” section, one called vnet0 and the other called vnet1.
In this example, I have defined the LAN on vnet0 192.168.6.0/24, and the router has the address 192.168.1.254 (a common default on many routers), so I've defined the DMZ on vnet1 192.168.1.0/24.
Note: From inside the Jail, these interfaces will be known as epair0b and epair1b rather than vnet0 and vnet1.
Preparing the Gateway Jail
1. Log in to your TrueNAS server as root using SSH or the Shell option of the TrueNAS Web Portal.
2. Make some decisions and define some variables.
# Tailor each of these examples for your own situation
JAIL_NAME="net" # name of the jail that will contain the gateway and firewall
LAN_INTERFACE="epair0b" # network device serving our LAN
LAN_NETWORK="192.168.6.0/24" # network address or our LAN
PUBLIC_INTERFACE="epair1b" # network device leading to the internet
CONF_DIR="/usr/local/etc/fw" # where we store the config
FIREWALL_CONF="${CONF_DIR:?}/firewall.conf" # firewall config file
NAT_CONF="${CONF_DIR:?}/nat.conf" # net service config file
Configure the Firewall
This is just a basic configuration, allowing all devices on the network to communicate with each other. You may want to add some extra rules of your own.
jexec "ioc-${JAIL_NAME:?}" \
mkdir -p "${FIREWALL_CONF%/*}"
jexec "ioc-${JAIL_NAME:?}" /bin/sh -c \
"cat >| ${FIREWALL_CONF:?}" \
<<END
# be quiet and flush all rules on start
-q flush
# allow local traffic, deny RFC 1918 addresses on the outside
add 00100 allow ip from any to any via lo0
add 00110 deny ip from any to 127.0.0.0/8
add 00120 deny ip from any to any not verrevpath in
add 00301 deny ip from 10.0.0.0/8 to any in via ${PUBLIC_INTERFACE:?}
add 00302 deny ip from 172.16.0.0/12 to any in via ${PUBLIC_INTERFACE:?}
add 00303 deny ip from 192.168.0.0/16 to any in via ${PUBLIC_INTERFACE:?}
# check if incoming packets belong to a natted session, allow through if yes
add 01000 divert natd ip from any to me in via ${PUBLIC_INTERFACE:?}
add 01001 check-state
# allow some traffic from the local net to the router
# SSH
add 04000 allow tcp from ${LAN_NETWORK:?} to me dst-port 22 in via ${LAN_INTERFACE:?} setup keep-state
# ICMP
add 04001 allow icmp from ${LAN_NETWORK:?} to me in via ${LAN_INTERFACE:?}
# NTP
add 04002 allow tcp from ${LAN_NETWORK:?} to me dst-port 123 in via ${LAN_INTERFACE:?} setup keep-state
add 04003 allow udp from ${LAN_NETWORK:?} to me dst-port 123 in via ${LAN_INTERFACE:?} keep-state
# DNS
add 04006 allow udp from ${LAN_NETWORK:?} to me dst-port 53 in via ${LAN_INTERFACE:?}
# DHCP
add 04007 allow udp from any to any dst-port 67 in via ${LAN_INTERFACE:?}
# drop everything else
add 04009 deny ip from ${LAN_NETWORK:?} to me
# pass outgoing packets (to be natted) on to a special NAT rule
add 04109 skipto 61000 ip from ${LAN_NETWORK:?} to any in via ${LAN_INTERFACE:?} keep-state
# allow all outgoing traffic from the router (maybe you should be more restrictive)
add 05010 allow ip from me to any out keep-state
# Drop everything that has come so far.
# This means it doesn't belong to an established connection.
# Don't log the most noisy scans.
add 59998 deny icmp from any to me
add 59999 deny ip from any to me dst-port 135,137-139,445,4665
add 60000 deny log tcp from any to any established
add 60000 deny log ip from any to any
# this is the NAT rule. Only outgoing packets from the local net will come here.
# First, nat them, then pass them on (again, you may choose to be more restrictive)
add 61000 divert natd ip from ${LAN_NETWORK:?} to any out via ${PUBLIC_INTERFACE:?}
add 61001 allow ip from any to any
END
Configure NAT
jexec "ioc-${JAIL_NAME:?}" \
mkdir -p "${NAT_CONF%/*}"
jexec "ioc-${JAIL_NAME:?}" /bin/sh -c \
"cat >| ${NAT_CONF:?}" \
<<END
unregistered_only
interface ${PUBLIC_INTERFACE:?}
use_sockets
dynamic
# dyamically open fw for ftp, irc
# punch_fw 2000:50
END
Activating the Configuration
# enable IP forwarding
jexec "ioc-${JAIL_NAME:?}" \
sysrc gateway_enable="YES"
# enable firewall
jexec "ioc-${JAIL_NAME:?}" \
sysrc firewall_enable="YES"
# name of firewall config
jexec "ioc-${JAIL_NAME:?}" \
sysrc firewall_type="${FIREWALL_CONF:?}"
# log more while testing, or be quiet in normal operation?
jexec "ioc-${JAIL_NAME:?}" \
sysrc firewall_quiet="YES"
# enable the NAT service
jexec "ioc-${JAIL_NAME:?}" \
sysrc natd_enable="YES"
# public gateway needs nat
jexec "ioc-${JAIL_NAME:?}" \
sysrc natd_interface="${PUBLIC_INTERFACE:?}"
# extra settings for nat
jexec "ioc-${JAIL_NAME:?}" \
sysrc natd_flags="-f ${NAT_CONF:?}"
# start the firewall & natd
jexec "ioc-${JAIL_NAME:?}" \
service ipfw start
Credits
This page has been cobbled together from various bits of information I've found on the Internet.